Information Security is the practice of defending information from unauthorized access, use, disclosure, modification or destruction. In today’s world, the proliferation of electronic media has brought a new level of awareness of both the plethora of available information and the dangers associated with not protecting it.
The Technology Department is always looking for tools to safeguard student and employee information. It takes a village, however, and our goal is to be a partner in the mission to both protect data and educate our community to be responsible for the information and data (personal and business-related) with which we come in contact every day.
Working to Protect
At Fitchburg State we are always working to keep the campus safe from cyber attacks. You may see these tools in use on your devices while going about your day-to-day.
- Multi-Factor Authentication - Helping to make sure you are the one logging into your account
- Endpoint Protection - Antivirus software is a key component to help keep your devices safe.
- Enterprise Firewalls and DNS security - These tools work to keep you safe when browsing the internet.
- DLP software - This works in tandem with encryption to make sure sensitive data on your system can be protected.
- Policies and planning - Keeping a handle on all the regulations needed to protect your data. Take a moment a review those that apply to you.
Information Security Awareness Training
The university provides training to employees as outlined in our Security Training and Awareness Policy.
The information security awareness training program aims to establish and sustain an appropriate level of protection for data and information resources by increasing users’ awareness of their information security responsibilities. Specific objectives include:
- Improving awareness of the need to protect information resources
- Ensuring users understand their responsibilities for protecting information resources
- Ensuring users are knowledgeable about the company’s information security policies
- Recognizing common threats and who to report them to. See our What to Watch Out For section below for tips.
Access Your Training
Emails are sent to users when they are enrolled in a new training campaign. To check on your own training, you can visit the Fitchburg State KnowBe4 Portal.
You can also do this by going through the login portal and clicking KnoweBe4 Security Awareness training. Once on the training site, click the Training tab and view your remaining training materials.
University Credentials / Passwords
Security experts always tell you to choose a long, complicated password, which preferably contains numbers and punctuation characters rather than just letters. Because a password, which consists of a combination of entries from a 26-character repertoire (a-z), is much easier to crack than if the range of characters is 52 (a-z and A-Z) or 62 (including digits too).
If you've ever wondered just how secure your favorite password is, here's a simple website that will tell you. Just go to How Secure is My Password (opens in new tab) and start typing. As you type, the indicator is updated after every character to tell you approximately how long a desktop PC typically takes to crack it.
At home, remember: it's far more convenient to choose a good password in the first place than it is to change it. You can write your passwords down and keep them in a safe location or use a program like Password Safe (opens in new tab).
The main reason for regular password changes is to limit your account's exposure to misuse. Whenever you type your password, it is at risk of compromise - by someone looking over your shoulder, through interception as it travels across the network, and possibly through a phishing scam. Have you ever shared your password with a friend or family member? If so, you might be inadvertently putting your information in unintended hands. Certainly, if you break up with someone with whom you've shared a computer, change them all!
If a hacker gets your password either by guessing or stealing it, he can access your network or account for as long as your password is valid. Updating your password every quarter significantly limits the utility of that password to an attacker.
If you suspect your account has been compromised, we strongly recommend you contact the Help Desk and change your password. This goes for personal accounts too. If you suspect a virus or malware on your phone, it is crucial to clean up the device before entering any other passwords on it.
When you sign into your account for the first time on a new device or app (like a web browser), you need more than just the username and password. You need a second thing - what we call a second "factor" - to prove who you are.
The three most common factors are:
- Something you know. Your password or a Pin on your phone
- Something you have. Your smartphone with an app or a secure USB Key
- Something you are. A fingerprint or facial recognition
MFA helps protect your account by proving you are who is logging in. If your password was compromised, then the attacker could log in from anywhere. With MFA, you can prevent an attacker from using your credentials without you knowing.
Some common MFA applications are Microsoft Authenticator and Duo.
Keeping track of passwords is a challenge many of us face in today's digital age. It is important to store passwords in a secure location that is easily accessible when needed, while also ensuring that they are encrypted. One solution to this issue is using a password manager. These applications allow you to store different passwords for various applications, while only requiring a single master password and multi-factor authentication for access. A few password manager options to look at are:
See our University Credentials page for information on how to change your password.
What to Watch Out For
Phishing attacks target YOU, the individual, with a sense of urgency. The goal of the attack is to get you to provide the attacker with information to access your account, your colleges account, or to send money somewhere. Once the attacker has the information, they pivot to identity theft, financial loss, or accessing sensitive information. With your credentials, the works their oyster!
To protect yourself - Think Before You Click
- Hover over the links in an email to see what website address each is pointing to.
- When in doubt, go directly to the website by typing the website address in your browser's address bar.
- Verify any urgent requests that come from a contact within your organization to confirm they are valid, particularly before transferring money or divulging information.
- Only open attachments that come from known senders.
- Never click/enable macros or content from unknown sources.
- Send any suspicious emails to phishtank@fitchburgstate.edu.
Vishing refers to voice phishing. It is a social engineering attack where criminals attempt to trick individuals into revealing sensitive information over the phone. They often use deceptive tactics to impersonate legitimate organizations like banks, government agencies, or IT support.
The callers are often armed with data from other breaches, making their requests seem legitimate. We need everyone to be extra vigilant—please review the following red flags and best practices to help safeguard our information.
Vishing Techniques to Look Out for:
- Urgent or Threatening Language: Scammers often try to create a sense of urgency or use fear tactics, claiming accounts are at risk or legal action is imminent.
- Non-Answers or Redirecting Questions: Be cautious if the caller dodges questions or tries to redirect the conversation when asked to clarify their identity.
- Requests for Sensitive Information: Scammers may ask for things like Students' ID numbers or what data we have on file. Most legitimate callers should not need this information. It’s better to lead them to the information on their own rather than divulging it.
How to Protect Yourself from Vishing:
- Ask for Full Caller Details: Always ask for the caller’s full name, contact information, and reason for calling before continuing with any request.
- Verify Identity Independently: Check the caller’s information using independent methods, such as looking up their contact details or verifying ID numbers. When in doubt, don’t proceed until you’ve confirmed their identity.
- Stay Calm and Consistent: Scammers rely on throwing you off guard, so following a consistent process can help prevent errors. Stick to our verification steps regardless of the caller’s tone.
- Limit Information Disclosure: Only provide information that is strictly relevant to the stated inquiry. If something seems off or irrelevant, notify the Technology Security team.
- Report Suspicious Calls: If you receive a suspicious call, open a Help Desk ticket (opens in new tab). Be sure to include all the details of the call. If you feel threatened or if the caller is aggressive, reach out to University Police as well. We’re here to mitigate risks, track trends, and work to prevent repeated scams.
Helpful Resources on Phone Scams
Just like phishing, smishing uses cell phone text messages to lure consumers in. Often the text will contain an URL or phone number. The phone number often has an automated voice response system. And again just like phishing, the smishing message usually asks for your immediate attention.
In many cases, the smishing message will come from a "5000" number instead of displaying an actual phone number. This usually indicates the SMS message was sent via email to the cell phone, and not sent from another cell phone.
Recently we have seen smishing messages being sent to alumni groups. Do not respond to smishing messages!
Ransomware (opens in new tab) is a form of malware designed to encrypt files on a device, rendering any files and the systems that rely on them unusable. Malicious actors then demand ransom in exchange for decryption. If you suspect your computer has been hit by ransomware, e.g. you start to see strange files on your computer, Turn off the computer and bring your laptop to the Help Desk or an IT professional.
To protect yourself:
- Ransomware commonly happens after a phishing attack. Be vigilant about suspicious links and not enabling macros from unknown sources.
- Update your computer and phone. Vulnerable applications and OSs are the targets of most ransomware attacks.
- Back up data regularly. Keep it on a separate device and store it offline. An external hard drive can be a great spot to keep family photos and documents in case of an attack.
SIM swapping is a type of fraud where an attacker convinces your mobile carrier to transfer your phone number to a new SIM card under their control. This allows them to intercept calls, texts, and most importantly, two-factor authentication (2FA) codes sent via SMS, giving them access to your online accounts, such as banking and social media.
This attack is one of the main reasons Fitchburg State recommends the Microsoft Authenticator app for Multi-Factor.
What to watch out for:
- No phone service: Your phone will show "No Service" or "SOS" in an area where you typically have a signal.
- Can't make or receive calls and texts: This is the most common symptom, as your service has been ported to another device.
- Unsolicited carrier messages: You may receive unusual text messages or emails from your mobile provider about an upcoming service or SIM change that you did not authorize.
- Floods of calls or texts: Scammers sometimes deliberately call or text your number repeatedly as a distraction technique to make you turn off your phone before they initiate the swap.
What you can do.
Use phishing-resistant Multi-Factor on important accounts. This includes options like Microsoft Authenticator or other MFA apps, FIDO2 usb security keys, Passkeys and platform MFA like Face ID or Touch ID.
Familiarize yourself with your carriers protections:
Data Classification
Data classification plays a vital role in structuring and safeguarding our information by organizing it according to sensitivity. By implementing a clear classification system, Fitchburg State can adopt appropriate security measures that not only ensure regulatory compliance but also safeguard against unauthorized access. This proactive approach to data classification significantly enhances our data governance practices and strengthens our ability to protect sensitive information effectively.
The WISP outlines different types of data we at Fitchburg State need to protect. To help quickly identify data risks, we have our institution's data classification policy on our internal policies page. It is the responsibility of all university members to abide by these policies.
Public, Internal, Restricted
These data classifications guide our approach to securing data. Additional information can be found in the data classification policy.
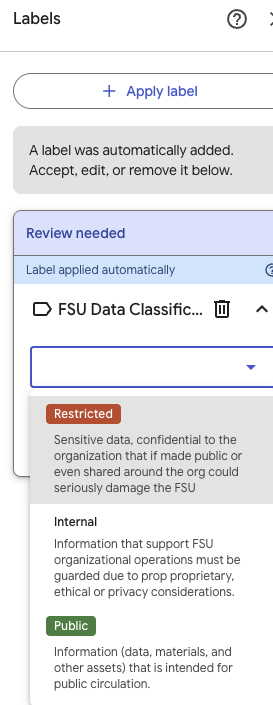
- Public: Information (data, materials, and other assets) intended for public circulation. This information may be freely disseminated without potential harm.
- Internal: Internal data is information that supports Fitchburg State University’s organizational operations and, therefore, must be guarded due to proprietary, ethical, or privacy considerations and must be protected from unauthorized access, modification, transmission, storage, or other use. This information is not intended for public use, and its unauthorized disclosure could adversely impact the company, customers, or employees.
- Restricted: Restricted Data includes information that Fitchburg State University has a contractual, legal, or regulatory obligation to safeguard in the most stringent manner. If made public or even shared around the organization, this information could seriously damage the organization, its employees, or its customers and could potentially be non-compliant with the Payment Card Industry Data Security Standard and applicable state or federal laws and regulations, such as Massachusetts Privacy Law (201 CMR 17.00) and NIST SP 800-171 Revision 3.
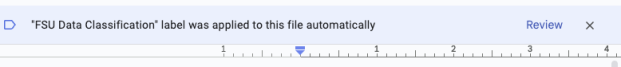
You will see a banner at the top of your drive documents stating "FSU Data Classification label was applied to this file automatically".
Clicking the Review text on the right brings up the Labels screen, where you can choose a label to apply to your file.
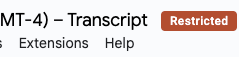
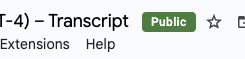
If you choose the Restricted or Public label, the document will also get a flag with its title indicating the classification.
Most documents and files will be labeled with the Internal label. We encourage you to change the label to a more appropriate one as needed.
You can also find the label screen through the File > Labels menu on the top right of your file.